ADFS Configuration
When you choose to select an IClaims authentication provider like ADFS or Azure, you will need to have the following configuration data available:
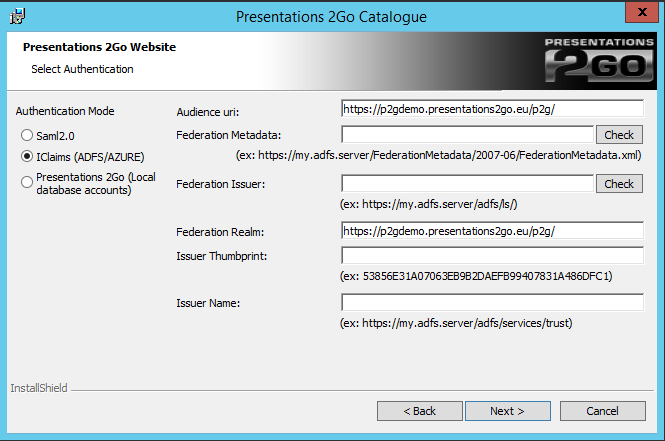
- Audience url eg: https://p2gdemo.presentations2go.server/p2g/
- Federation metadata eg: https://my.adfs.server/FederationMetadata/2007-06/FederationMetadata.xml
- Federation issuer eg : https://my.adfs.server/adfs/ls
- Federation realm eg: https://p2gdemo.presentations2go.server/p2g/
- Issuer thumbprint: eg: 53856E31A07063EB9B2DAEFB99407831A486DFC1
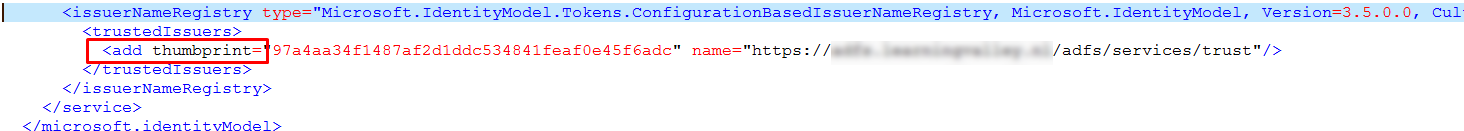
- Issuer name eg: https://my.adfs.server/adfs/services/trust
- You can find the Issuer Thumbprint on the ADFS server (see screenshot below).
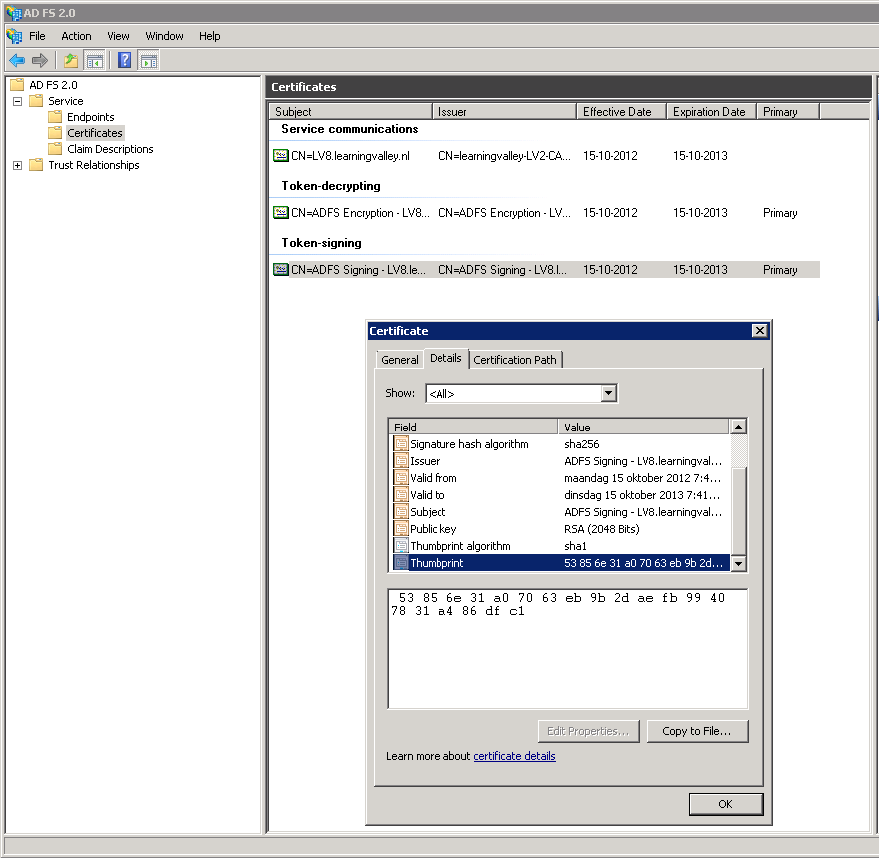
It is stored in the certificates section in the Token-Signing certificate.
- Select the Thumbprint value
- Remove all spaces and convert it to uppercase. (so “53 85 6e 31 a0 70 63 eb 9b 2d ae fb 99 40 78 31 a4 86 df c1” will be “53856E31A07063EB9B2DAEFB99407831A486DFC1”)
The installer will create the metadata file in C:\inetpub\wwwroot\P2G\FederationMetadata\2007-06\FederationMetadata.xml. You will need this file on the ADFS server to setup the “Relaying Trust Party”
A super user account can be assigned in the next screen. Use a valid email address of the user you wish to grant the super user right. A super user bypasses the normal roles and rights assigned in the Presentations 2go server.
When using ADFS for authentication, the account the website is running under (normally Network Service) needs to have access to the private key of the SSL certificate. To enable this run the certificate snapin (WindowsKey-R and type mmc)
Choose File/Add/remove Snap-in
Choose Certificates and Add
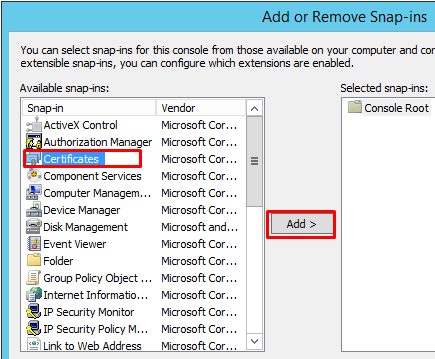
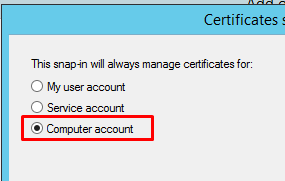
Choose computer account in the next popup
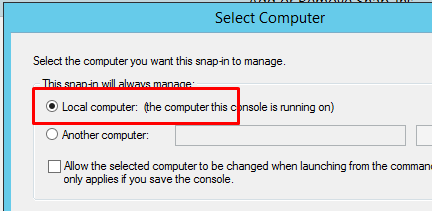
And Local computer after you press Next
Press Finish and Ok
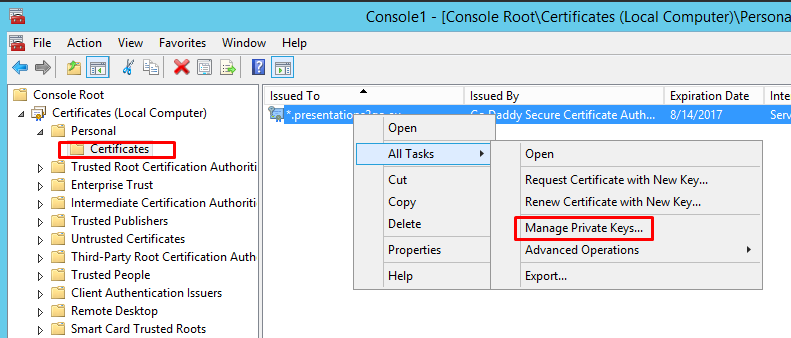
Now navigate to Personal/Certificates, Select the certificate and right click to select All Tasks/Manage Private Keys
Add Network Service to the security settings with default permissions.
NOTE: you will need to follow the same method when you replace the IIS SSL certificate! Furthermore, if the subject/find value changes you will need to change that in the web.config file in c:\inetpub\wwwroot\p2g. See below.