Connect to ADFS using SAML2 authentication
ADFS can be used in combination with Presentations2Go Server in 2 ways:
- ADFS claims based authentication.
- SAMLv2 claims based authentication.
This document describes the steps to use ADFS authentication using SAMLv2.
We assume use have your ADFS server configured.
When installing Presentations2Go Server you have the choice to select 3 different authentication methods:
- Local (database) accounts
- ADFS Claims based authentication
- SAML v2 based authentication
We assume you selected option 3 (SAML v2)
Configure the Presentations2Go video server
In c:\wwwroot\inetpub\wwwroot\p2g\web.config (on your Presentations2Go Server) you will find a SAML20Federation section (bottom of the file). This has been prepopulated from the Presentations2Go installer with values you supplied during installation.
<SAML20Federation xmlns="urn:dk.nita.saml20.configuration">
<ServiceProvider id="https://demo.presentations2go.eu/p2g/" server="https://demo.presentations2go.eu/p2g/">
<ServiceEndpoint localpath="/p2g/login.ashx" type="signon" redirectUrl="/p2g/cataloguepage.aspx" index="0" />
<ServiceEndpoint localpath="/p2g/logout.ashx" type="logout" redirectUrl="/p2g/signoutnew.aspx" index="1" />
<ServiceEndpoint localpath="/p2g/metadata.ashx" type="metadata" />
<md:ContactPerson contactType="administrative" xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata">
<md:Company>MyCompany</md:Company>
<md:GivenName>MyName</md:GivenName>
<md:SurName>MySurname</md:SurName>
<md:EmailAddress>MyEmail</md:EmailAddress>
<md:TelephoneNumber>MyPhone</md:TelephoneNumber>
</md:ContactPerson>
</ServiceProvider>
<RequestedAttributes>
<!-- The attributes that the demonstration identity provider issues. -->
<att name="urn:mace:dir:attribute-def:uid" isRequired="true"/>
<att name="urn:mace:dir:attribute-def:displayName"/>
<att name="urn:mace:dir:attribute-def:mail"/>
<att name="urn:mace:dir:attribute-def:eduPersonTargetedID"/>
<att name="urn:mace:dir:attribute-def:eduPersonAffiliation"/>
<att name="urn:mace:dir:attribute-def:sn" />
<att name="urn:mace:dir:attribute-def:cn" />
</RequestedAttributes>
<IDPEndPoints metadata="C:\inetpub\wwwroot\P2G\Metadata">
</IDPEndPoints>
</SAML20Federation>
The IDPEndpoint element could contain extra elements but you only need to supply these if the Identyprovider supplies the metadata.xml in the correct format.
<IDPEndPoints metadata="C:\inetpub\wwwroot\P2G\Metadata">
<add id="https://MyADFSServer/FederationMetadata/2007-06/FederationMetadata.xml">
<CertificateValidation>
<add type="dk.nita.saml20.Specification.SelfIssuedCertificateSpecification, dk.nita.saml20" />
</CertificateValidation>
</add>
<add id="https://engine.test.surfconext.nl/authentication/idp/metadata">
<CertificateValidation>
<add type="dk.nita.saml20.Specification.SelfIssuedCertificateSpecification, dk.nita.saml20" />
</CertificateValidation>
</add>
</IDPEndPoints>
So leave out the yellow part.
Configuring the relying trust party
Open the ADFS management console on the ADFS server and select the “Relying Party Trusts” menu and select “Add Relying Party Trust”.
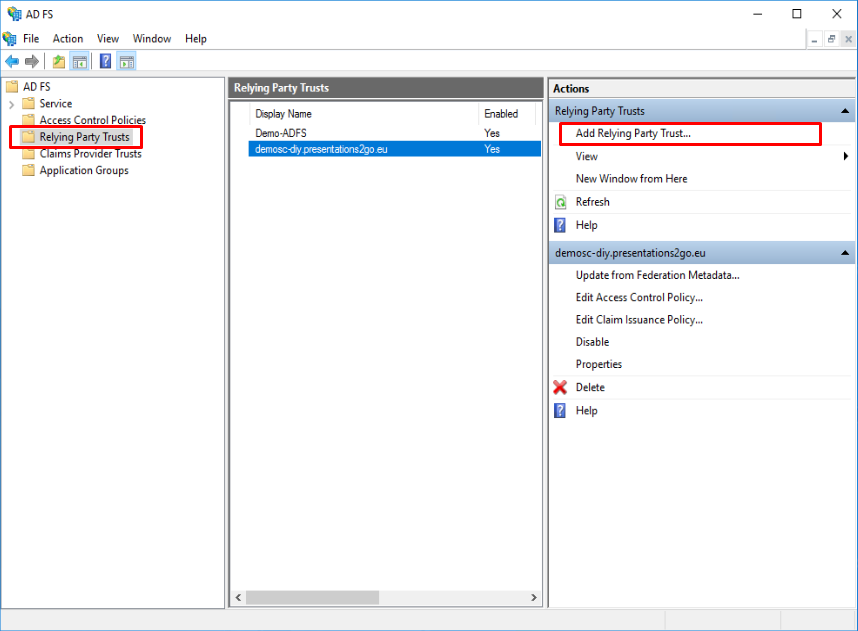
This will bring up a wizard that will navigate you through the various steps.
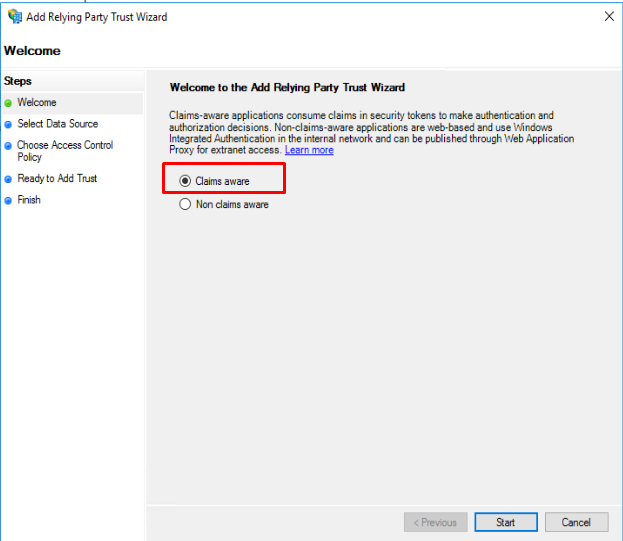
Enter the location of the Metadata on your Presentations2Go Server. This is always:
https://myPresentations2GoServer/P2G/metadata.ashx
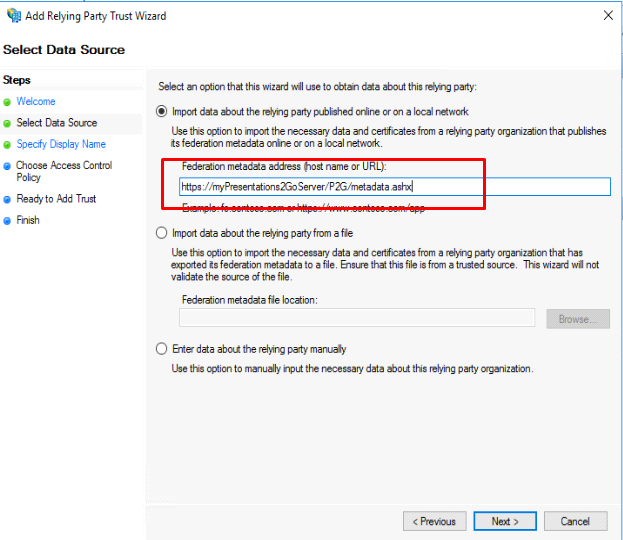
Give it a display name and add notes if desired.
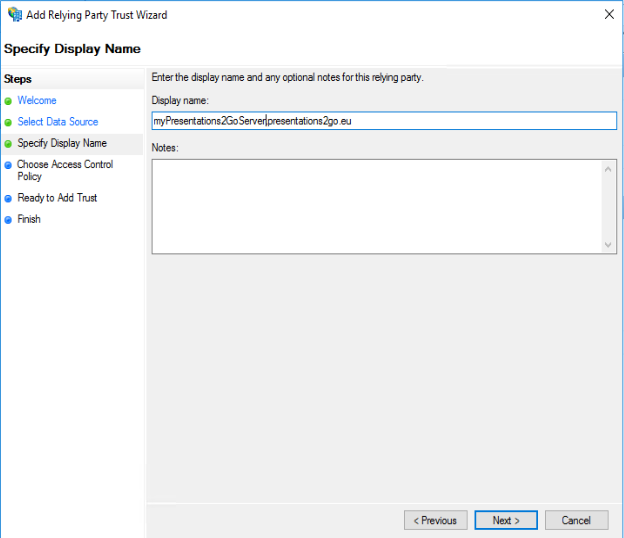
Define the access control policy. If you Permit Everyone, you can modify this later if required
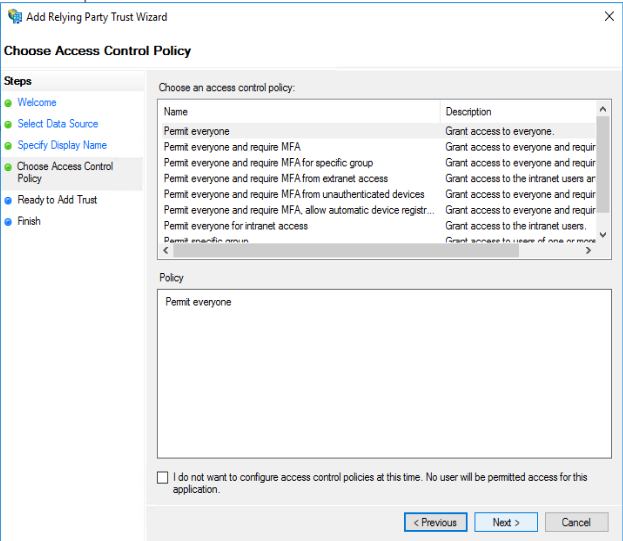
And you will be shown a summary of the configured setting
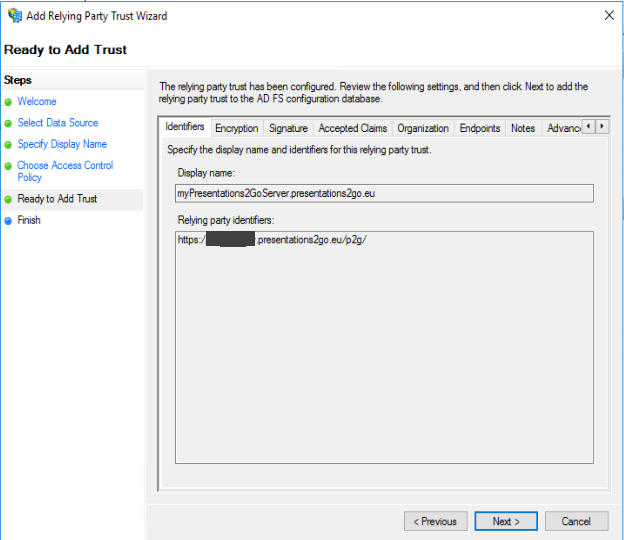
And finish up.
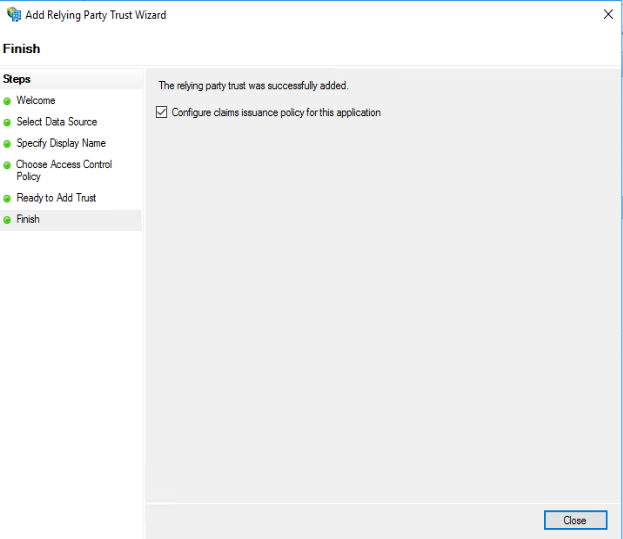
Because the checkbox in the above screenshot was checked, the Claims Issuance Policy dialog will open if you press Close.
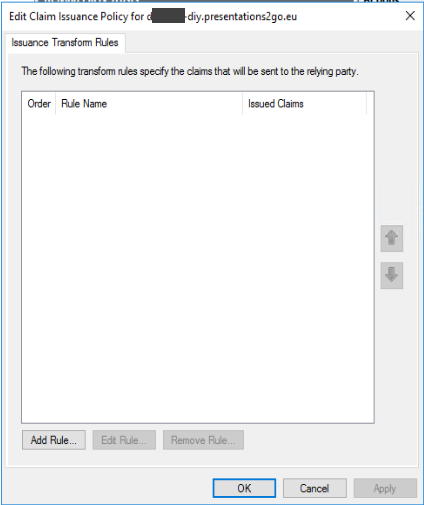
In this dialog you need to define the claims that will be send to the Presentations2Go server once a login is performed.
Add each of the following claims:
LDAP Attribute |
Outgoing Claim Type/Claim Rule Name |
Given-Name |
urn:mace:dir:attribute-def:givenName |
Common-Name |
urn:mace:dir:attribute-def:cn |
Surname |
urn:mace:dir:attribute-def:sn |
E-Mail-Addresses |
urn:mace:dir:attribute-def:mail |
Display-Name |
urn:mace:dir:attribute-def:displayName |
SAM-Account-Name |
urn:mace:dir:attribute-def:uid |
User-Principal-Name |
Name ID |
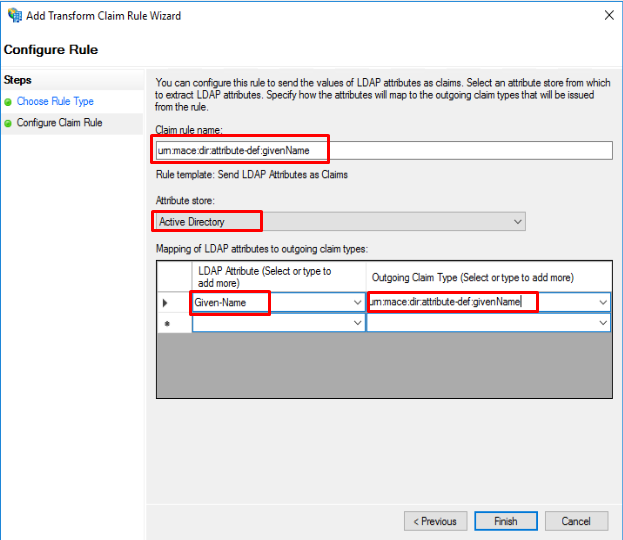
If you do not add the “Name ID” attribute, the AuthnStatement will not have a SessionIndex and that will throw an error when trying to login to The Presentations2Go Catalogue.
The following attributes are optional
Group Membership |
Affiliation |
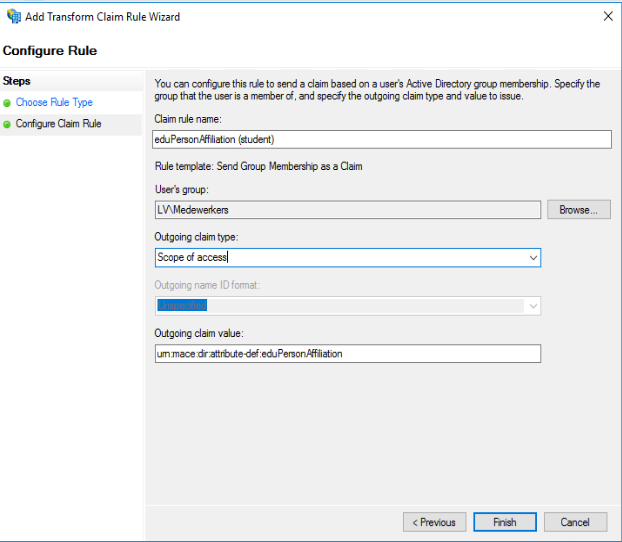
eduPersonAffiliation (student) |
urn:mace:dir:attribute-def:eduPersonAffiliation |
eduPersonAffiliation (employee) |
urn:mace:dir:attribute-def:eduPersonAffiliation |
schacHomeOrganization |
urn:mace:terena.org:attribute-def:schacHomeOrganization |
The next step is to change the “Secure Has Algorithm” to SHA1.
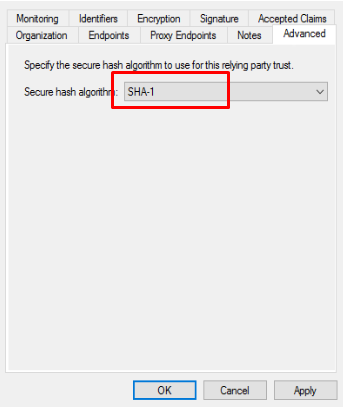
If you don’t want the assertion data encrypted, you will need to remove the “Encryption Certificate”. If the assertion is encrypted, you won’t be able to monitor the data with saml browser plugins (for debugging).
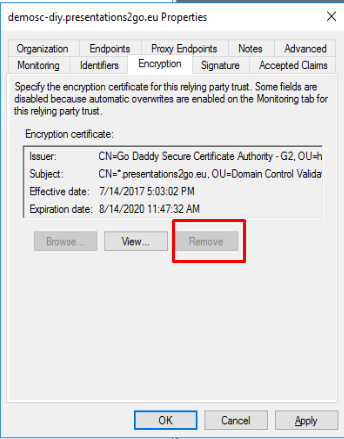
By default the encryption certificate cannot be removed because “Monitor Relying party” is enabled.
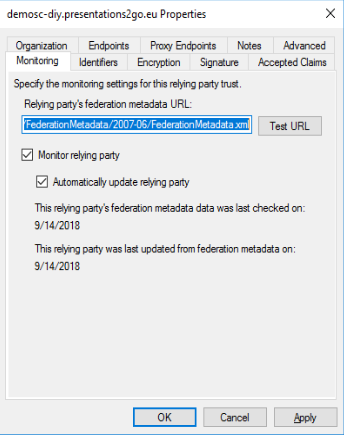
Uncheck the Monitor checkbox and remove the certificate in the Encryption tab.
Get the metadata
You will have to get the metadata from the ADFS server and store this in c:\inetpub\wwwroot\p2g\metadata\ as metadata.xml
The Standard metadata.xml file is the one used for Surfconext connectivity and you need to replace that with your own.
You can retrieve the metadata file from : https://MyADFSServer/FederationMetadata/2007-06/FederationMetadata.xml
Copy that into the c:\inetpub\wwwroot\p2g\metadata\ folders and edit it to make some changes.
Find and replace rsa-sha256 with rsa-sha1. The ADFS metadata defaults to sha256 but presentations2Go Server cannot handle that yet. Sha256 occurs twice in the metadata file.
The metadata.xml should be CR/LF formatted (so change it if it is unix/lf formatted).
For readability it is advised to XML reformat the file in and editor like ultraedit or notepad++.
Once you made the changes, iisreset the webserver and try to login.
If login succeeds, type https://myPresentations2GoServer/P2G/logininfo.aspx to check if all claims have been correctly passed on to the Presentations2Go Server.