Common configuration errors for saml2.0
Certificate find error
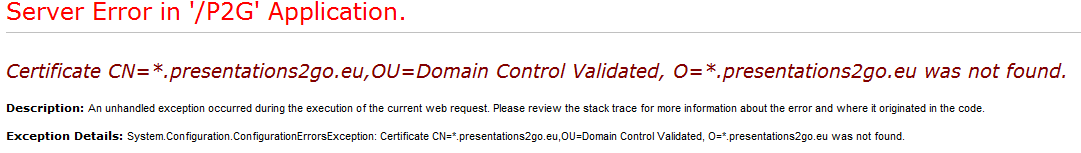
The cause of this error is the formatting of the following value in web.config:
<SigningCertificate findValue="CN=*.presentations2go.eu,OU=Domain Control Validated, O=*.presentations2go.eu" storeLocation="LocalMachine" storeName="My" x509FindType="FindBySubjectDistinguishedName" />
In the highlighted text you see there is no space character between the comma and OU. It should be there.
<SigningCertificate findValue="CN=*.presentations2go.eu, OU=Domain Control Validated, O=*.presentations2go.eu" storeLocation="LocalMachine" storeName="My" x509FindType="FindBySubjectDistinguishedName" />
Error after login
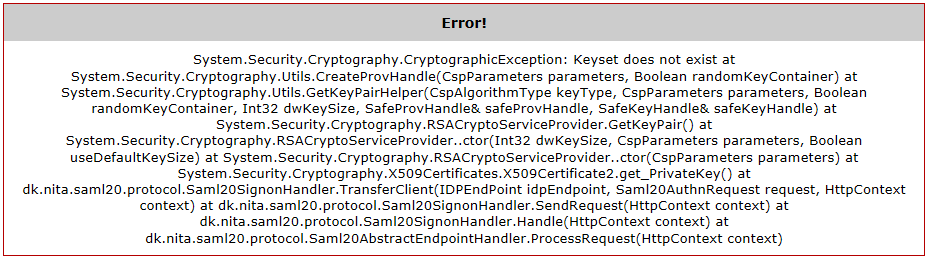
This error means the certificate cannot be read by the application.
To solve this, you need to give NetworkService account access to the private key (See 2 above).
The signature of the incoming message is invalid
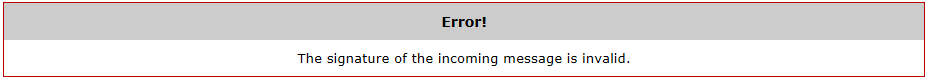
This error is caused by the saml server (IdP) adding a signature in their metadata.
This can be solved either by making sure the signature is in the metadata or by ignoring the SignatureCheck.
To ignore the signaturecheck change web.config <IDPEndPoints> element setting:
<add id="https://My.SamlServer.com/authentication/idp/metadata">
to
<add id=" https://My.SamlServer.com" omitAssertionSignatureCheck="true">
Subject still cannot be found
In some situations, the certificate cannot be read using the x509FindType="FindBySubjectDistinguishedName". In that case you can use another method to find the certificate for example by using x509FindType= x509FindType="FindByThumbprint". Of course you will need to supply the thumbprint as the SigningCertificate findValue
HandleAssertion: The signature of the incoming message is invalid
After completing the login process you get the following error message:
HandleAssertion: The signature of the incoming message is invalid.
This is caused by the IdP not using a valid certificate for assertion. Probably a self signed certificate was used.
This can be fixed by allowing self signed certificates for assertion.
In c:\inetpub\wwwroot\p2g\web.config find the following section and change DefaultCertificateSpecification into SelfIssuedCertificateSpecification
<IDPEndPoints metadata="C:\inetpub\wwwroot\P2G\metadata\">
<add id="https://engine.test.surfconext.nl/authentication/idp/metadata">
<CertificateValidation>
<!--<add type="dk.nita.saml20.Specification.DefaultCertificateSpecification, dk.nita.saml20"/>-->
<add type="dk.nita.saml20.Specification.SelfIssuedCertificateSpecification, dk.nita.saml20" />
</CertificateValidation>
</add>
</IDPEndPoints>
Save the web.config and try again.
Debugging
Debugging SAML and ADFS authentication issues can be a difficult task.
To help in finding the cause of authentication issues you can enabled tracing functionality in Presentations2Go Server by adding some settings to the web.config file in c:\inetpub\wwwroot\p2g\web.config
Once you add the tracing settings to web.config (either Saml or Adfs) a log will be written in the temp folder.
Be sure to create the folder first and make sure the NetworkService account has write access to that folder (or if you run the web application under another account, make sure that account has write access to the folder).
The settings can be added to the web.config eg at the end just before the closing </configuration> element.
Once you save the web.config, the application pool will automatically reset and the settings will take effect immediately.
SAML2
<system.diagnostics>
<trace autoflush="true" ></trace>
<sources>
<source name="dk.nita.saml20" switchValue="Verbose">
<listeners>
<add name="trace"/>
</listeners>
</source>
</sources>
<sharedListeners>
<add name="trace" type="System.Diagnostics.XmlWriterTraceListener" initializeData="C:\temp\Saml2Log.xml"/>
</sharedListeners>
</system.diagnostics>
ADFS
<system.diagnostics>
<sources>
<source name="Microsoft.IdentityModel" switchValue="Verbose">
<listeners>
<add name="xml" type="System.Diagnostics.XmlWriterTraceListener" initializeData="C:\Temp\ADFSLog.xml" />
</listeners>
</source>
</sources>
<trace autoflush="true" />
</system.diagnostics>